Technology & Security
End-to-end competence from the idea to the finished product
ekey relies on a continuous value chain from the idea to the finished product. The range extends from the technology to the overall concept: Continuous competence and the highest demands on the products ensure quality.
The latest technology
ekey fingerprint scanners use state-of-the-art technology with an area sensor. The company’s access solutions thus correspond to the current technological status that users already know quite well from their everyday lives, such as from smartphones. Using the fingerprint scanner is therefore particularly intuitive and is especially appreciated for its user-friendly touch operation. Minor injuries on the finger or the growth of children’s fingers are not a problem for the recognition.
The highest security standards
ekey guarantees the highest standards of product security and protection against misuse and unauthorized access to access control systems. In the development, design and manufacture of the products, ekey takes into account the recommendations and guidelines on access control systems of the Federal Office for Information Security (BSI) and those of VdS Schadenverhütung GmbH.


“As Austria’s largest non-university research institution, the AIT Austrian Institute of Technology deals with infrastructure topics of the future. We accompanied ekey in the development of the ekey bionyx app and got to know the company as very innovative and motivated.”
Dr. Daniel Slamanig, Scientist
AIT Austrian Institute of Technology GmbH

“Microsoft stands for forward-looking cloud solutions. We are very pleased to support ekey with our Azure services in the development of innovative access control systems. ekey places the highest demands on its solutions – we place the highest demands on the security of our cloud services – a perfect match.”
Mag. Robert Voitleithner, Senior Customer Program Manager
Microsoft Österreich GmbH

“I consult companies that place high demands on the IT security and privacy of their customers. At ekey, I really appreciate the fact that data protection and security are not just promised, but are taken into account and implemented throughout the entire ‘Secure Software Development Lifecycle’.”
DI Andreas Happe, Founder
Andreas Happe

“Software and information technology are playing an increasingly important role in our society and economy and also require appropriate quality management. At ekey, we have already been able to establish valuable know-how, e.g. using agile methods, requirements engineering and software architecture, which contributes to ongoing improvement and quality enhancement in software development. Thank you for the many years of good cooperation!”
Dipl.-Ing. Johannes Bergsmann, Managing Partner
Software Quality Lab GmbH
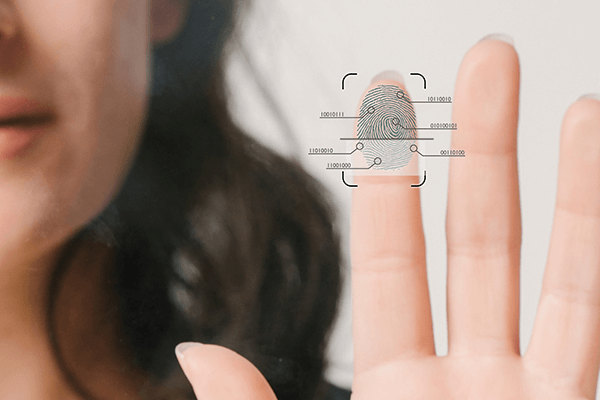
Patented algorithm
ekey fingerprint scanners use a recognition algorithm that converts and stores characteristic features such as unique dots, minutiae (e.g. line endings, bifurcations, etc.) and other specific line properties into an encrypted numeric code. In order to ensure outstanding recognition, additional specially developed procedures are used via the patented ekey algorithm. Based on the latest findings, the algorithm has been optimized for use with the latest sensor technology.
Two components, one goal
The ekey algorithm is divided into two main components, the Feature Extractor and the Matcher. The common goal of these two components: security around the clock.
1. Feature Extractor: Fingerprints detected by the sensor are blurry, have poor contrast, and sometimes contain errors and glitches. The algorithm developed by ekey uses very powerful measures to improve the image quality accordingly and to be able to reliably extract characteristic features.
2. Matcher: The actual recognition engine works very quickly and reliably. Based on many years of experience and extensive research, the ekey algorithm stands for outstanding security with unique convenience. The core technology can be used with both small and large databases.
Quality “Made in Austria”
Before an ekey product can be launched on the market, it has to undergo a rigorous endurance test: intensive simulations ranging from blazing heat and freezing cold to high humidity. Each fingerprint scanner and all of its components must successfully complete these tests numerous times before the product finally finds its way into the customer’s hands.
ekey’s formula for quality consists of the highest standards of functionality, reliability, and security, which are refined through extensive testing – certified quality “Made in Austria”:
- TÜV certified quality management system in accordance with EN ISO 9001:2015
- Extensive production, manufacturing, and functional testing (zero tolerance)
- Testing for environmental and temperature resistance
- Vibration and shock-tested
- Tested for penetration of water and mechanical parts
- CE-compliant


Convenience meets security
Fingerprint scanner access systems from ekey enrich everyday life with the convenience of keyless access as well as flexibility and smart features. Security is always at the center of this process. So how secure is an ekey fingerprint scanner system? Here you will find answers to the most common frequently asked questions:
Can the system be manipulated by exchanging the fingerprint scanners ?
No, the system cannot be manipulated by exchanging the fingerprint scanners . Because fingerprint scanner and control panel are “married” during commissioning and communicate in encrypted form. The created user data is saved with the serial number of the device. If the fingerprint scanners is exchanged or the system is expanded, this must be verified by an administrator in the ekey bionyx app. The saved fingers are retained and do not have to be saved again. Stored data cannot be transferred to another device without this process.
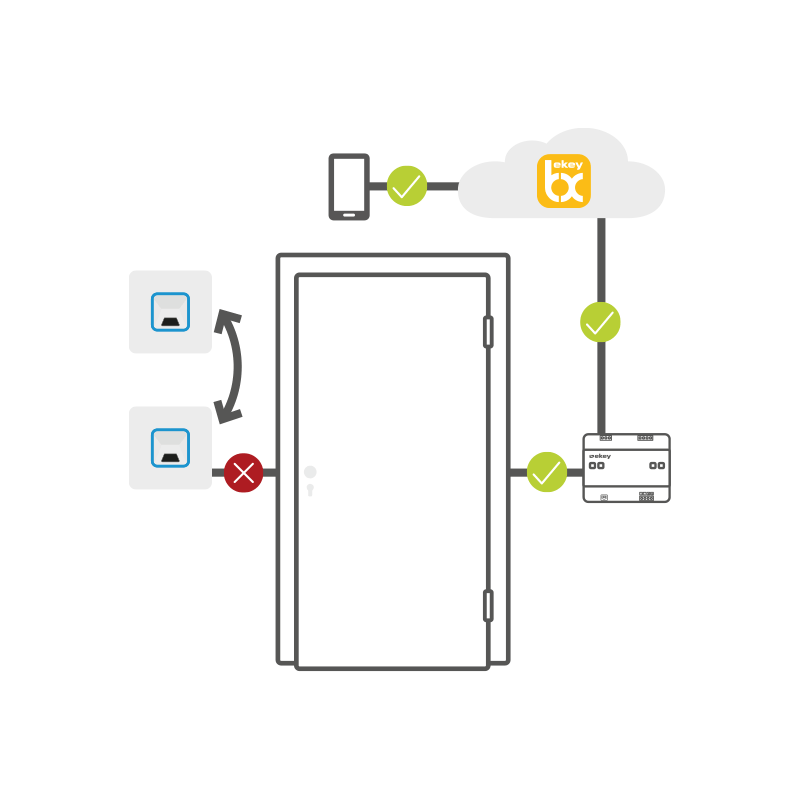
Can the ekey fingerprint scanner access solution be manipulated from the outside so that the door opens?
No. The system cannot be manipulated from the outside. Not even through the use of force, because the fingerprint scanner and the control panel are spatially separated.
The opening impulse comes from the control panel, which is located in the protected interior area.
The data is also encrypted and secured multiple times at all times.
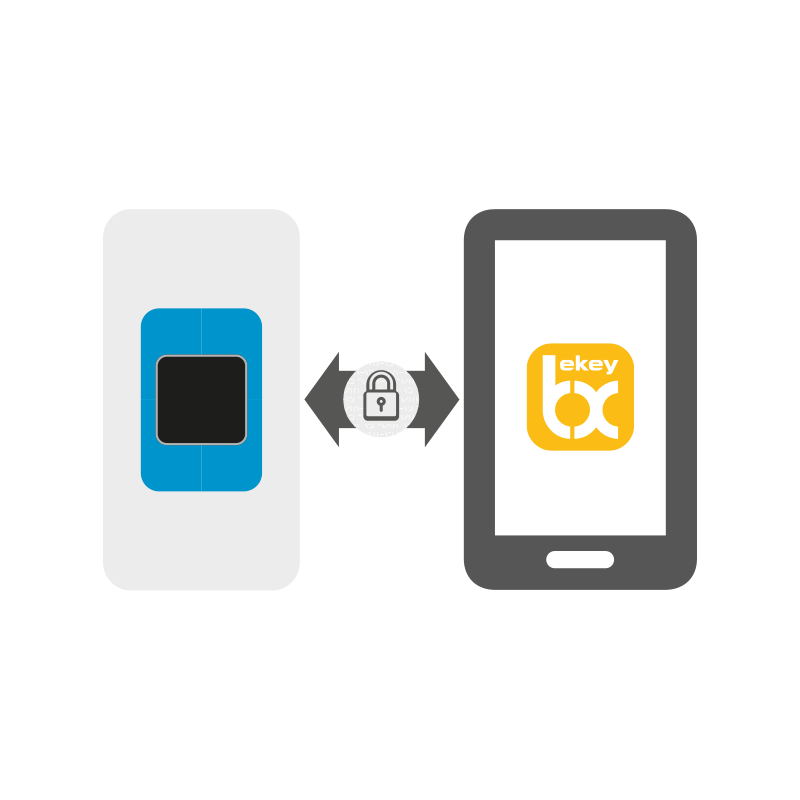
Data transmission in the ekey bionyx system is end-to-end encrypted. All data is transmitted encrypted across all transmission stations.

Can a door open by itself in the event of a power failure?
Only an authorized user can trigger this opening command.

Are hidden access authorizations for the manufacturer stored in the system?

Why does ekey rely on a cloud solution?
In addition to the actual device – the hardware – an access control system always also includes the corresponding software – from computing and storage capacities to the actual software. With the ekey bionyx cloud, ekey has decided to use cloud-based technology because it offers numerous advantages on the software side (ekey bionyx app):
1. Data protection: Leading providers of cloud-based solutions make great financial and human investments to protect their customers’ data. Therefore, such a solution is usually more professional in this respect than an in-house solution.
2. Security: The business model of large cloud providers is based on data being stored securely. Therefore, both the data centers themselves are optimally protected (e.g. premises, surveillance, fire protection, etc.) and the virtual protection against cybercrime is at a correspondingly high level.
3. Availability: Software level agreements can guarantee software availability of around 99% (the missing 1% is mostly planned downtime for updates). Comparably high availability is not possible with your own server.
4. Updates: Software must always be kept up to date in order to offer maximum security. Cloud-based access systems are always up to date and updates are automatic.

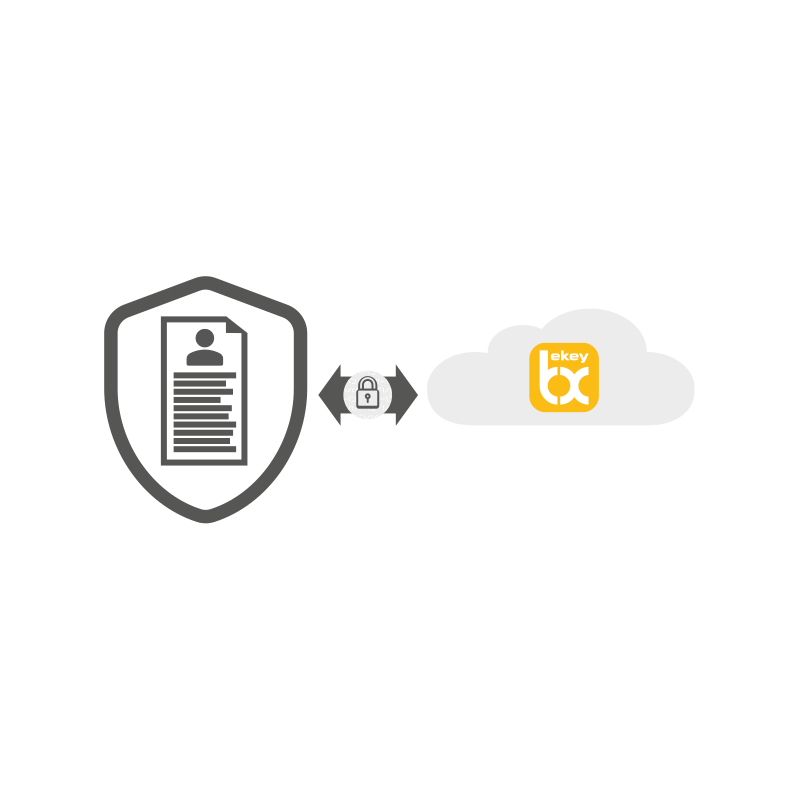
What happens to the personal data?
What happens if I lose my smartphone or tablet?
So even if the mobile device is lost, it is still possible to log in using a new device with the access data.

Are fingerprint scanner activities logged?

Are fingerprints stored?
No. ekey does not store fingerprints.
A pattern is created from the biometric features of the original fingerprint, such as the unique dots, line endings, and forks – the so-called template.
This is converted into a unique binary number code by the specially developed and patented software algorithm, and is saved and used for comparison each time.
The templates are stored encrypted in the ekey bionyx cloud.
The key to this is only on your own end device (smartphone/tablet), so the data is protected from unauthorized access. The security can be compared to that of a netbanking app.
What is the probability that the door will open for an unauthorized person?
In summary: It is theoretically possible for an unauthorized person to gain access to ekey fingerprint scanners , but it is extremely unlikely. An ekey system is 1,000 times more secure than the four-digit code on an ATM card. And the probability of landing a lottery six (6 out of 45) with one tip is 1:8,145,000, which is significantly higher than that of an unauthorized person gaining access .
How do you open the door in the event of a power failure?
It keeps the fingerprint scanner, the control panel and the motorized lock in operation for several hours. Alternatively, a key can of course be used at any time.
And even if the connection to the Internet or the router fails, the door can still be opened.

Is there insurance protection with a fingerprint scanner access solution ?
Is the system connected to the Internet?
Due to the high security standard, only encrypted WLAN networks can be used.

Is it possible to make a usable fake finger to open a door from a fingerprint left (e.g. on a glass)?
In addition, it is almost impossible to create a usable fake fingerprint. With a lot of criminal energy, even more expert knowledge, and the best laboratory conditions, the characteristics could be transferred to a fake finger.
Conclusion: possible in theory, hardly likely in practice.
Can an original fingerprint be reconstructed from the stored data?
How secure is the connection between smartphone or tablet, fingerprint scanner and control panel?
Data is transferred in the ekey bionyx app using end-to-end encryption. All data is transmitted in encrypted form across all transmission stations. The data sent cannot be read or generated by attackers or by ekey itself.